Risk Assessment
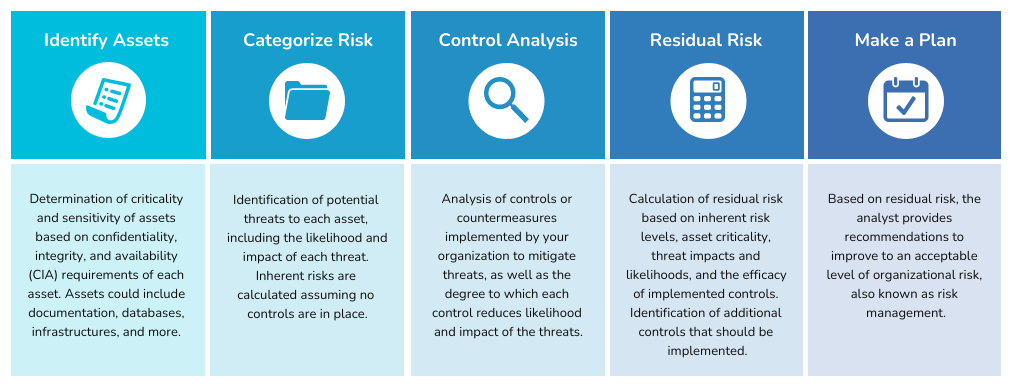
Our Methodology
Tiered Risk Assessment Offerings
TraceSecurity developed the following tiered risk assessments to meet security and compliance requirements. Based on the size and maturity of your organization, we will dedicate our risk assessment efforts to the controls that require the most attention for security and risk mitigation, and your examiners. Each of these risk assessments can be further customized to include additional security controls as needed.
-
![Tier 1]()
Tier 1
A Tier 1 Risk Assessment includes identification of 100+ controls that your organization has in place to reduce the likelihood and impact of cybersecurity events. This risk assessment has been optimized - and priced - for smaller organizations to maintain security and compliance with ease.
-
![Tier 2]()
Tier 2
A Tier 2 Risk Assessment includes identification of 150+ controls that your organization has in place to reduce the likelihood and impact of cybersecurity events. This risk assessment was designed for medium-sized organizations, or those of average or evolving cybersecurity maturity.
-
![Tier 3]()
Tier 3
A Tier 3 Risk Assessment includes identification of 200+ controls that your organization has in place to reduce the likelihood and impact of cybersecurity events. This risk assessment is best suited for mature organizations that tend to have more complicated IT infrastructures.
