North Korea-aligned threat actor, Lazarus Group, has been reported using Linux malware for the first time in its Operation DreamJob campaign. ESET researchers discovered the campaign targeting users with the end goal of distributing the SimplexTea Linux backdoor. This new development strengthens the ties between Lazarus and the recent 3CX supply-chain attack, further highlighting the group's growing cyber capabilities.
3CX Supply-Chain Attack
3CX, an international VoIP software developer and distributor, provides phone system services to organizations in various sectors. In March 2023, per a Reddit post, it was discovered that the desktop application for both Windows and macOS contained malicious code that allowed attackers to download and run arbitrary code on all machines where the application was installed. The investigation promptly established that 3CX did not incorporate the code but that 3CX had been breached. External threat actors employed the software of 3CX in a supply-chain attack to disseminate further malware to 3CX clients.
Operation DreamJob
Operation DreamJob, a series of campaigns attributed to the Lazarus Group, uses social engineering techniques to compromise its targets. The group lures victims with fake job offers from industry leaders, usually through LinkedIn or spear phishing.
In March 2023, a user in Georgia submitted a ZIP archive called "HSBC job offer.pdf.zip" to VirusTotal (Figure 1). The archive contained a single file: a native 64-bit Intel Linux binary written in Go named "HSBC job offer․pdf."
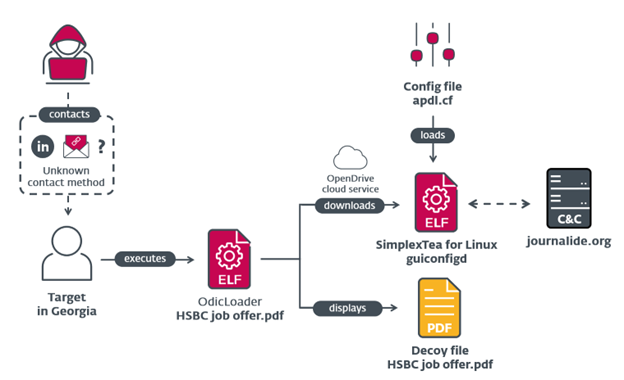
The attack occurs in three stages (Figure 2): The victim downloads the decoy PDF document. While the file looks like a normal .pdf file, Lazarus used a Unicode leader dot to trick the operating system. By opening the fake PDF, the victim opens an ELF downloader, dubbed OdicLoader, a malware that infects Linux-based systems by downloading and executing malicious code. An HSBC Job Offer.pdf is called using xdg-open and then displayed within the user’s preferred PDF viewer. At the same time, OdicLoader downloads a second-stage backdoor from OpenDrive and stores the SimplexTea backdoor in ~/.config/guiconfigd. Lastly, OdicLoader modifies ~/.bash_profile to execute the SimplexTea backdoor silently by appending >/dev/null 2>&1 to the execution command.
Attribution of the 3CX Supply-Chain Attack to Lazarus
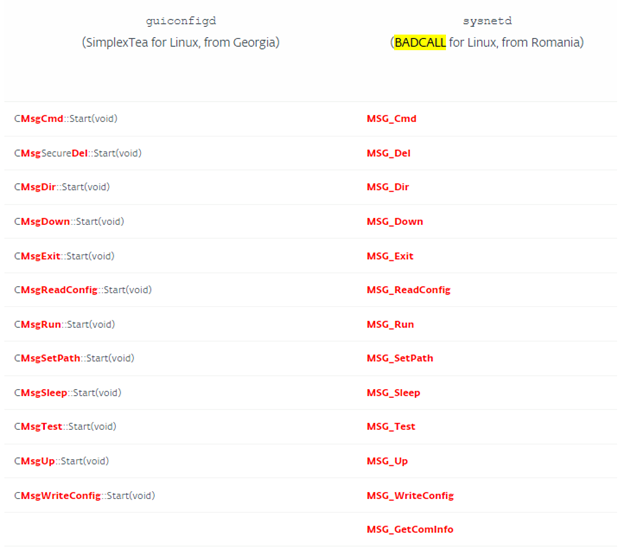
BADCALL, a 2018 attack, was attributed to Lazarus group by CISA. Knowing this, ESET compared guiconfigd from Operation DreamJob to sysnetd from BADCALL. SimplexTea backdoor appears to be an updated version of sysnetd rewritten from C to C++ (Figure 3).
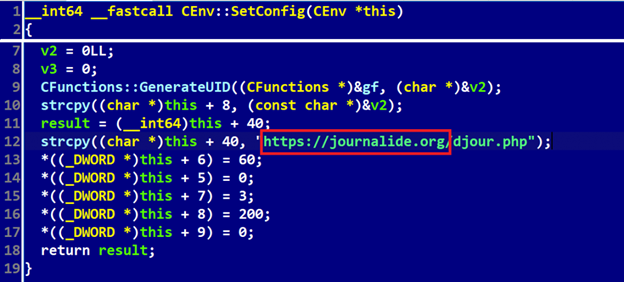
SimplexTea and 3CX attacks also utilized a shared domain for Command and Control (C2), journalide.org. Journalide.org is one of four C2 domains used in the 3CX attack. When ESET examined SimplexTea, it observed a hardcoded URL pointing to jourlanide.org (Figure 4). The use of journalide.org has helped confirm with a high level of confidence that Lazarus conducted the recent 3CX supply-chain attack.
Conclusion
The discovery of the Lazarus Group's first-ever Linux malware in the Operation DreamJob campaign highlights the group's expanding cyber capabilities and ability to target all major desktop operating systems. The strong link between Lazarus and the 3CX supply-chain attack showcases the threat actor's willingness to exploit multiple platforms to compromise victims and further their objectives.
Organizations and individuals should remain vigilant in the face of these evolving threats. Increased awareness of social engineering techniques, particularly spear phishing and direct messaging on professional networking platforms, is essential in defending against such attacks.