Modern Spear Phishing Emails
October 08, 2021
Introduction
Social engineering attacks continue to be the largest threat to the cybersecurity of organizations, with phishing campaigns being a powerful and common attack vector. With basic information security training, most users are aware that they should not click on links or download attachments from outside sources. They know not to trust emails that promise free iPads or gift cards, but modern attackers are more cunning and have evolved their tactics to better target unsuspecting users. Instead of sending disreputable phishing campaigns, they create spear-phishing campaigns, which are emails targeted at a specific individual or department within an organization that appears to be from a trusted source. In this article, we will walk you through some of the information gathering techniques and social engineering strategies that an attacker could use to craft a unique spear-phishing campaign against your company using only publicly available information. We will demonstrate this by crafting an example spear-phishing email for a fake institution named “Trace’s Local Credit Union.”
Reconnaissance
The first step in planning a spear-phishing campaign is reconnaissance. Many companies make this step easy for an attacker by making their information easily accessible on their company website. For example, the “Contact Us” section of a website can potentially list the names and contact information of branch managers and executives. An attacker may use this information to determine who they will mimic in a spear-phishing campaign attack. Modern phishing software gives attackers the ability to spoof, or imitate, the address from which an email is coming from, and an attacker could use this to impersonate a trusted member at an organization and trick its employees. In our example, Trace’s Local Credit Union provided the contact information for their branch manager “Sarah Brown” as well as their email address sbrown@tracelocalcu.org so that clients and potential vendors can contact her if needed.
The best solution to this public-information problem is to conceal any information such as email addresses or contact information from your web site. If it is necessary to provide your clients an email address on your website, then it is common practice to use addresses such as contact@tracelocalcu.org or info@tracelocalcu.org instead of personal contact information. Although this approach reveals the domain of your company’s email addresses (tracelocalcu.org), it prevents the attacker from having a direct contact to impersonate. This approach also prevents the attacker from learning the naming nomenclature of your company’s email addresses, which could be useful in the next step of the attack.
A skilled attacker can collect information on the users at an organization from around the internet using an email address domain, or even just a company name. An attacker may be able to find a list of users who work at a bank by simply searching the company name on sites like Google or LinkedIn. For our example, the user “John Stone” has a LinkedIn page which shows that he is a loan manager at Trace’s Local Credit Union as of one year ago. The attacker now knows a user to target, their department, and using their previous reconnaissance on Sarah, the attacker can infer that the user’s company email is jstone@tracelocalcu.org.
Spear Phishing
It is hard to mitigate this risk, especially for larger companies with large numbers of users; however, it is important to understand that this information is out there. This pool of accessible information is called a “spear-phishing attack surface” which can be identified through a penetration test that simulates an attackers methods to gather publicly available information. This test provides the company with a list of users who have been discovered using public information gathering techniques and will allow the company to assess the risk as they see fit. It is also important to train your employees on acceptable use of their company email. If an employee is using their company email to sign up for unnecessary, non-work-related websites or applications, it becomes much easier for an attacker to access this information.
Now that the attacker has a user to imitate and a user to attack, they can begin the delivery of the spear-phishing campaign. Attackers are aware that users are less likely to click on any links or download attachments if they are immediately suspicious. That is why modern attackers use social engineering tactics that establish a trust with their victim before delivering their malware. In our example, the attacker could send an email to John from Sarah that looks like this:
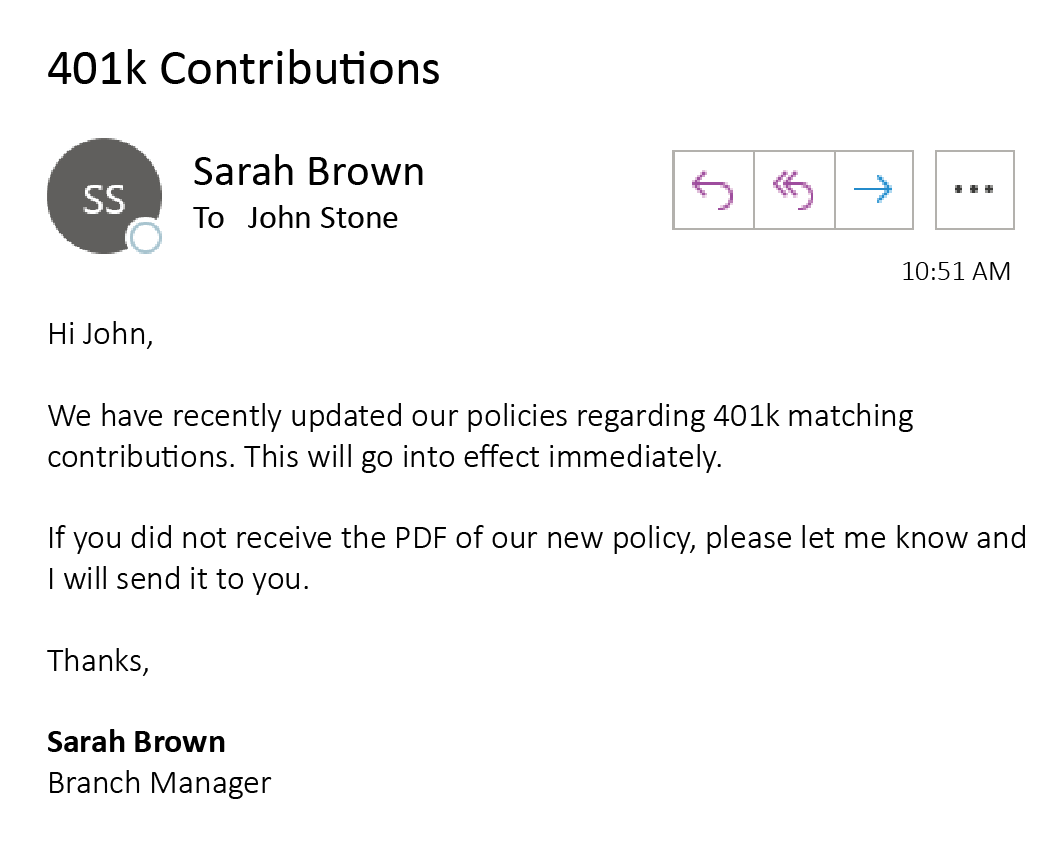
This tactic works to establish a trust with the user because it is coming from a trusted source and not revealing any evidence of an attack. The attack also uses the manipulation factor of urgency by stating that this new policy will “go into effect immediately.” After the trust has been established between the victim and the attacker, then the attacker will send the PDF containing malware.
Mitigation
There are several approaches to mitigate the deliveries of these types of attacks. One approach is to make sure that you have no outward facing email servers that an attacker could use to send this email to a user internally. Another approach is to make sure that Implicit Deny whitelisting is put in place so that attackers cannot send your users emails so easily. But these approaches are only preventative in the delivery of the email.
Ultimately, your investigation and mitigation activities should be driven by your organization's information security policies. It is important to train users to be cautious when clicking on any links or downloading attachments from an email, regardless of who they come from. Attackers will use many different techniques to trick users, and users should notify their IT departments of any emails that seem suspicious before trusting them. Please feel free to reach out to your account team or email us at info@tracesecurity.com if you have any further questions about spear-phishing.
References:
Gavin Debetaz, Information Security Analyst
Gavin has been honing his cybersecurity testing skills with TraceSecurity for over 3 years. Starting as an Associate Information Security Analyst, he focused on performing penetration testing, vulnerability assessments, phishing, and vishing engagements. Once promoted to a full-time Information Security Analyst, Gavin now also performs IT security audits and onsite social engineering tests. He earned a Bachelor of Science in Computer Science from Louisiana State University and currently holds a certification in Security+.